
Analyses user risk profiles | Invokes right number and types of authentication factors | Reduces friction with low-value assets | Protects high value assets | Positive user experience
E-Lock AdaptAuth is an AI-powered Adaptive Multi-factor Authentication solution. AdaptAuth uses a combination of real-time evaluation of contextual factors and statically configured authentication policies to determine the selection and flow of MFA factors for every individual authentication request.
This is achieved by building a risk profile for every user by analyzing past authentication attempts and behavioral patterns. The extent of deviation from such patterns invokes additional MFA factors until desired levels of identity assurance are achieved.
Through such intelligent adaption of authentication flows AdaptAuth achieves the right balance between security and user experience.
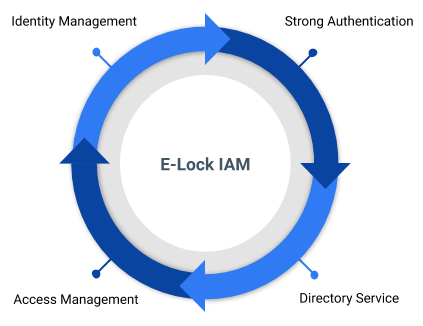
Identity and access management (IAM) in enterprise IT is a discipline which allows authorized individuals to access right resources at right time for right reasons.
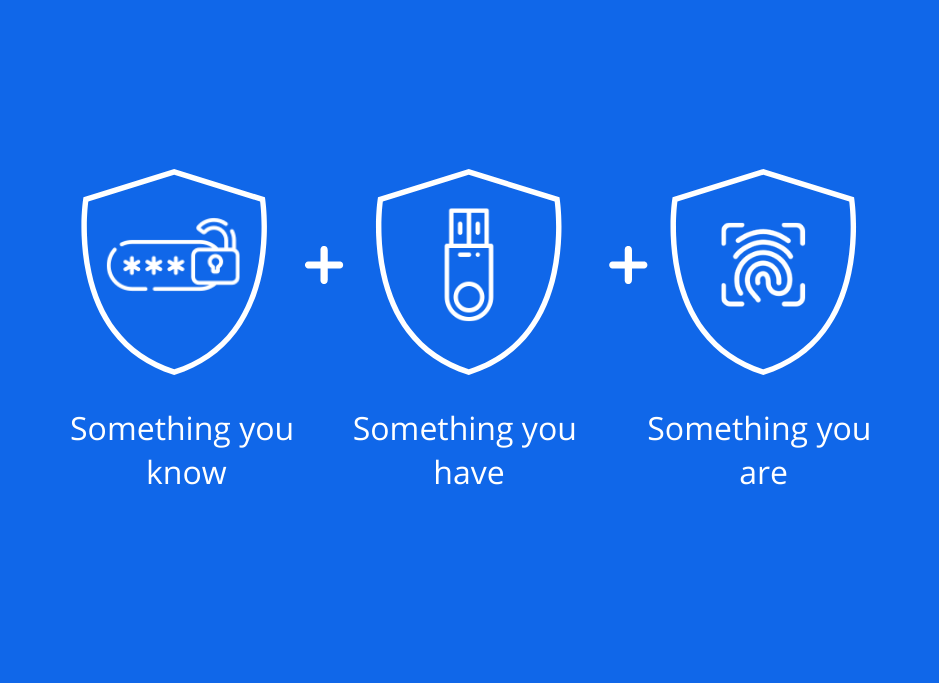
E-Lock MFA is a fully configurable authentication flow for your business and security requirements
E-Lock AMFA is an AI-Powered Adaptive Multi-factor Authentication that analyses user risk profile and automatically adapts the types and flow of authentication factors.
E-lock AMFA achieves the right balance. Analyses user risk profiles and invokes the right number and types of authentication factors. Reduces friction with low-value assets. Protects high value assets all while maintaining a positive user experience.
Provides essential functionalities of an authentication server. Manage user identities, implement basic authentication, 2FA and Single-Sign On (SSO).
Custom authentication flows based on different business requirements. Select from multiple ready-to-use authentication factors beyond basic authentication.
Configure authentication policies based on organizational requirements.
Our AI-powered anomaly detection and classification mechanism evaluates risk associated with each authentication attempt based on numerous context parameters such as IP addresses, geo-locations, device signatures and user behaviour patterns.
A device registration, identification, remembering and tracking mechanism to allow safer access from anywhere both for devices issued by organisation and BYOD.
Real-time monitoring and reporting of authentication requests and events.








Fill in the details below to let us know about your requirements